“Can you save my keys?”
At a crypto conference, someone approached me with a question:
“I have a friend who cannot remember the password for their app with [crypto custody tech provider]. Can you help them save their crypto? Its a few million dollars and they will give you 30% if you can help them.”
I was already familiar with the platform he mentioned. I told him I’m pretty sure he’s going to need that password.
Obviously wanting to help his friend, he asked: “will you please just talk to them?”
I agreed.
The call was short. My hunch was right — no password, no access.
That password encrypted the keys on his device. Not even the provider could help.
Now he’s clinging to a device, hoping one day the encryption will be broken… and that quantum computing doesn’t steal his fortune first.
One thing I want to mention up front: this is a cautionary tale for everyone. Banks, wealth advisors, exchanges, funds, DeFi protocols - have all been very real data points when it comes to crypto losses related to custody. This is not just a retail problem.
Quick wins in crypto custody
Setting up proper crypto custody can feel daunting. As the opening story shows, even seasoned crypto managers can lose everything through simple operational failures.
The gold standard is a full audit. Under the CCSS framework — the crypto custody audit standard — there are roughly 70 separate controls. For some operators, being ready for all of them on day one is difficult.
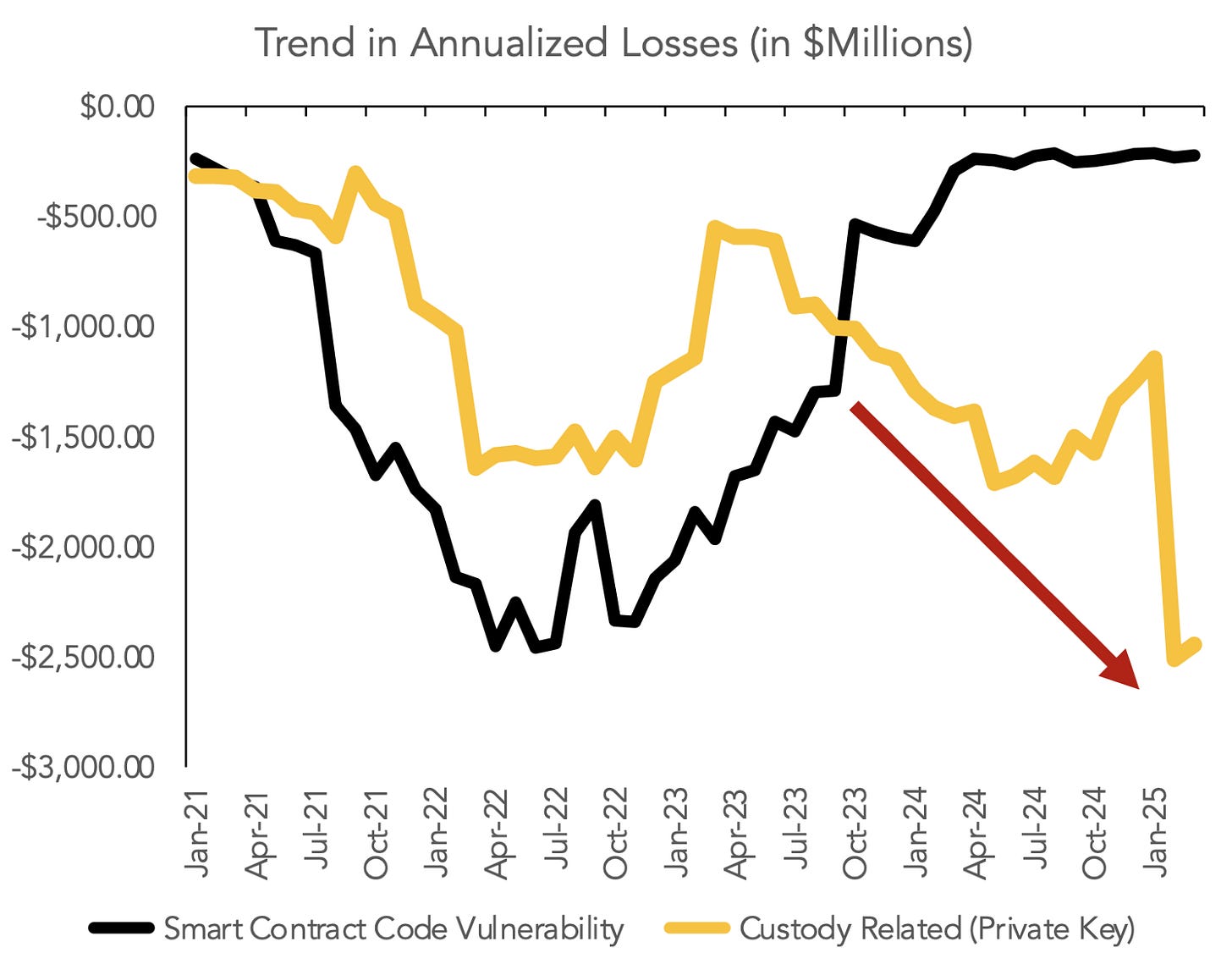
But the risk is real, and worth taking seriously. The data is clear: operational losses from custody failures remain a major drain on the industry, exceeding the damage caused by smart contract exploits. (The chart below, from Q1 of this year, shows the rolling yearly loss trend — still highly relevant today.)
Good news. You can still make meaningful improvements without all 70 controls (though they are extremely highly recommended). Here are a few quick wins teams can implement quickly.
1. Test your backups… Seriously.
Unfortunately, losing access to crypto because of not properly testing backup procedures is too common. It isn’t just examples like the guy I met at the conference.
Prime Trust, a regulated crypto custodian, went bankrupt in 2023 because they did not test their private key backups.
Ideally yearly at a minimum, you should test your backup keys.
Depending on *how( you’ve stored the them, you may even be able to verify a backup without fully recovering the keys (a safer option that avoids the risk of exposing sensitive key material during the test). But if you do go through a full recovery, treat it like a live exercise, assuming attackers could be watching and secure the process accordingly.
You can build your own processes for this, or use service providers. Ultimately, even if you choose the service provider route, there are critical operations you are still responsible for that you will *not* be able to offload.
2. Inventory your keys, backups, and who has access to devices
This one seems obvious, until you’re running your crypto operation, spinning up new wallets, integrating new custody providers, and launching on fresh blockchains.
Pretty soon you’re dealing with dozens (or hundreds or thousands) of wallets, across multiple providers, with backups scattered around for all of it.
Then you have a turnover in staff.
Then the new staff doesn’t know your prior CTO had a key signing device (maybe a phone specifically for signing transactions) that they stored in a drawer in their office.
Was the key material wiped from that device?
Do they still have the device?
What keys does that device give them access to?
3. Verify you’re signing the right transaction… every time.
It’s easy to assume that the transaction in front of you is the one you intended to sign. Attackers count on that.
In 2024, Bybit was a victim of the Lazarus Group hackers who tricked them into approving a malicious transaction. They believed they were signing something routine. Instead, they authorized a transfer the attacker controlled.
Again, even experienced teams are at risk.
Without getting too technical, an easy win here is to verify transaction details with multiple clients (e.g., run the transaction material through multiple softwares to see if they are giving you the same output for the expected transaction).
Close your gaps before someone else finds them.
At Digital Opportunities Group, we conduct risk assessments, in-depth operational due diligence (ODD), and CCSS audits to evaluate digital asset infrastructure. Our focus is on identifying operational gaps, custody risks, and regulatory blind spots, so investors can make informed decisions with confidence.
Some of our reports are available through Counterparty Catalogue, where users can explore over 100 service provider profiles, request due diligence assessments, and share or read feedback from industry peers, and more.
Recent ODD Reports:
More reports coming soon!
To learn more, contact us at info@digopp.group.
Disclaimer
We, Digital Opportunities Group Enterprises, Inc. are not providing investment or other advice. Nothing that we post on Substack should be construed as personalized investment advice or a recommendation that you buy, sell, or hold any security or other investment or that you pursue any investment style or strategy.
Case studies may be included for informational purposes only and are provided as a general overview of our general investment process. We have compiled our research in good faith and use reasonable efforts to include accurate and up-to-date information. In no event should we be responsible or liable for the correctness of any such research or for any damage or lost opportunities resulting from use of our data.
We are not responsible for the content of any third-party websites and we do not endorse the products, services, or investment recommendations described or offered in third-party social media posts and websites.
Nothing we post on Substack should be construed as, and may not be used in connection with, an offer to sell, or a solicitation of an offer to buy or hold, an interest in any security or investment product.